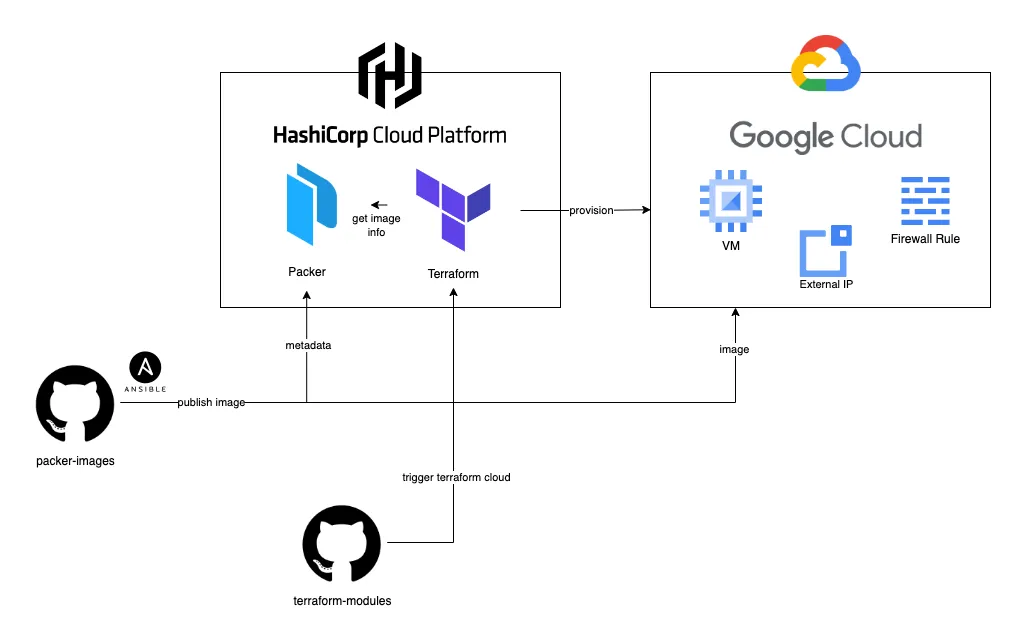
In the previous article, I explained how to create machine images using Packer and GCP. In this one, I’m going to explain how to deploy them using Terraform Cloud.
Google Cloud Configuration
Here we just need a Service Account with Editor Permissions. You can create one as I’ve explained in the previous article “Creating pipelines using Gitlab CI for Terraform and GCP”.
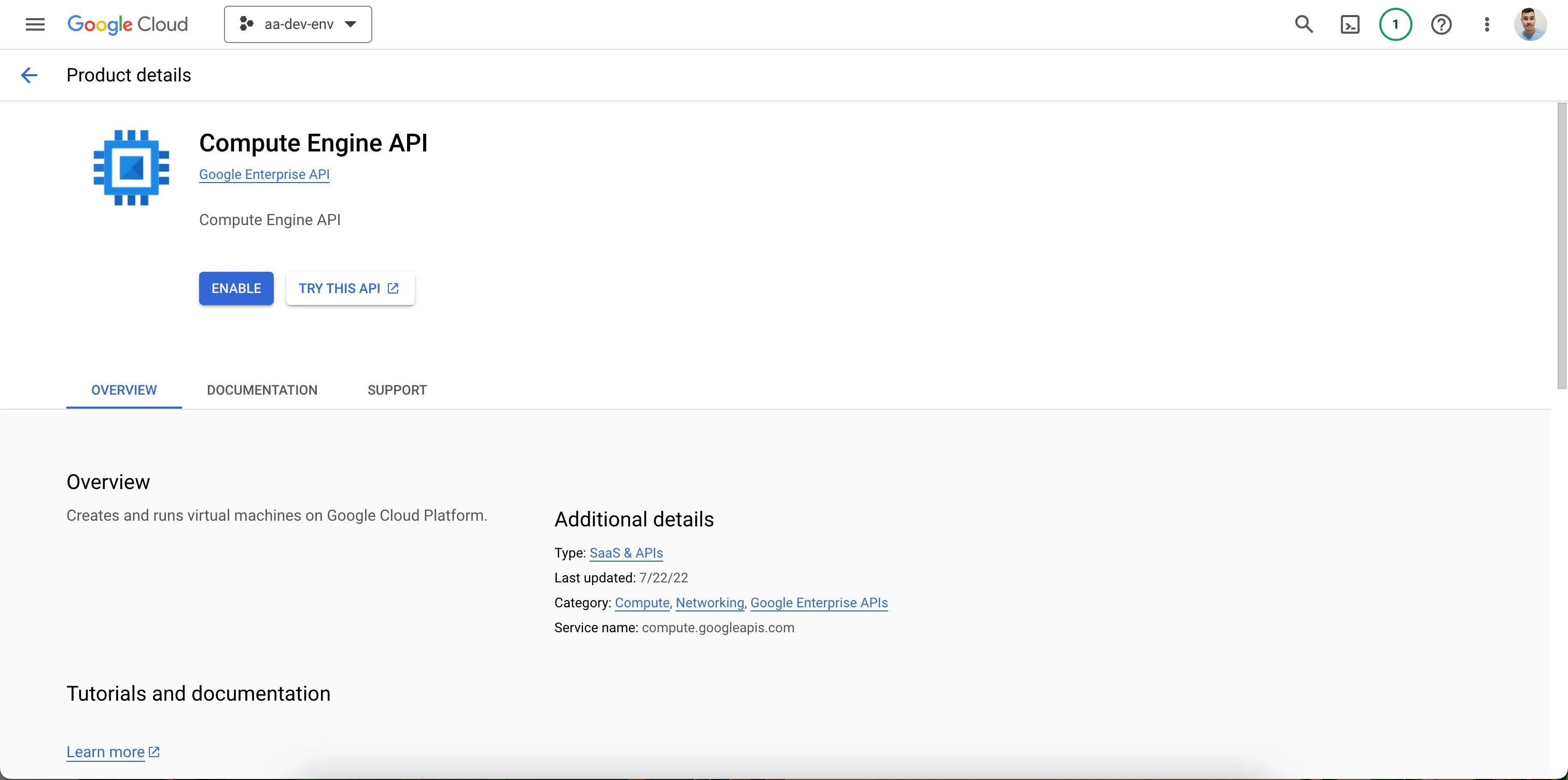
Please also enable the Compute Engine API.
As we published the images in the “DevOps” project, if we would like to use them in other projects we need to Grant Permission to the default Google API SA from the target projects in our “DevOps” project as “Image User”. Please follow the official documentation: Using Images from Other Projects.
Terraform Cloud Configuration
First, create two variable sets, one for HCP credentials and another one for GCP credentials.
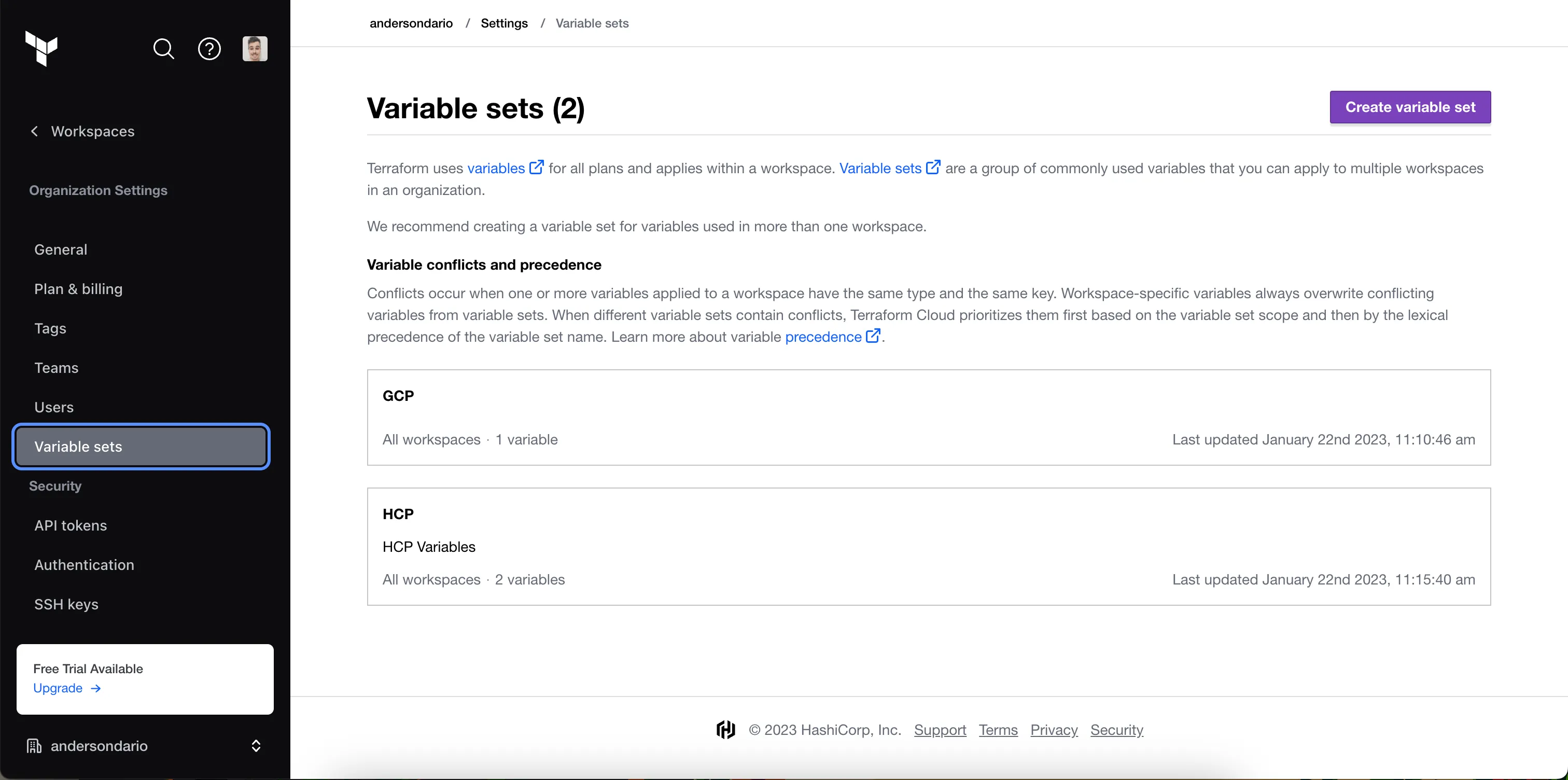
Variable Sets
GCP
- Variable:
GOOGLE_CREDENTIALS - Value: Service Account Json without line breaks.
- Type: Sensitive
- Category: Environment
HCP
- Variables:
HCP_CLIENT_IDandHCP_CLIENT_SECRET - Value: Create a Hashicorp Cloud Service Principal in IAM Section and use those values.
- Type: Sensitive
- Category: Environment
Now, let’s configure the workspace.
- Go to the home page, Create a Project (or use the default one), and then a workspace, for example:
Project Terraform Modules
- I am using my terraform-modules repo as example, and creating a workspace called dev of type VCS Workflow.
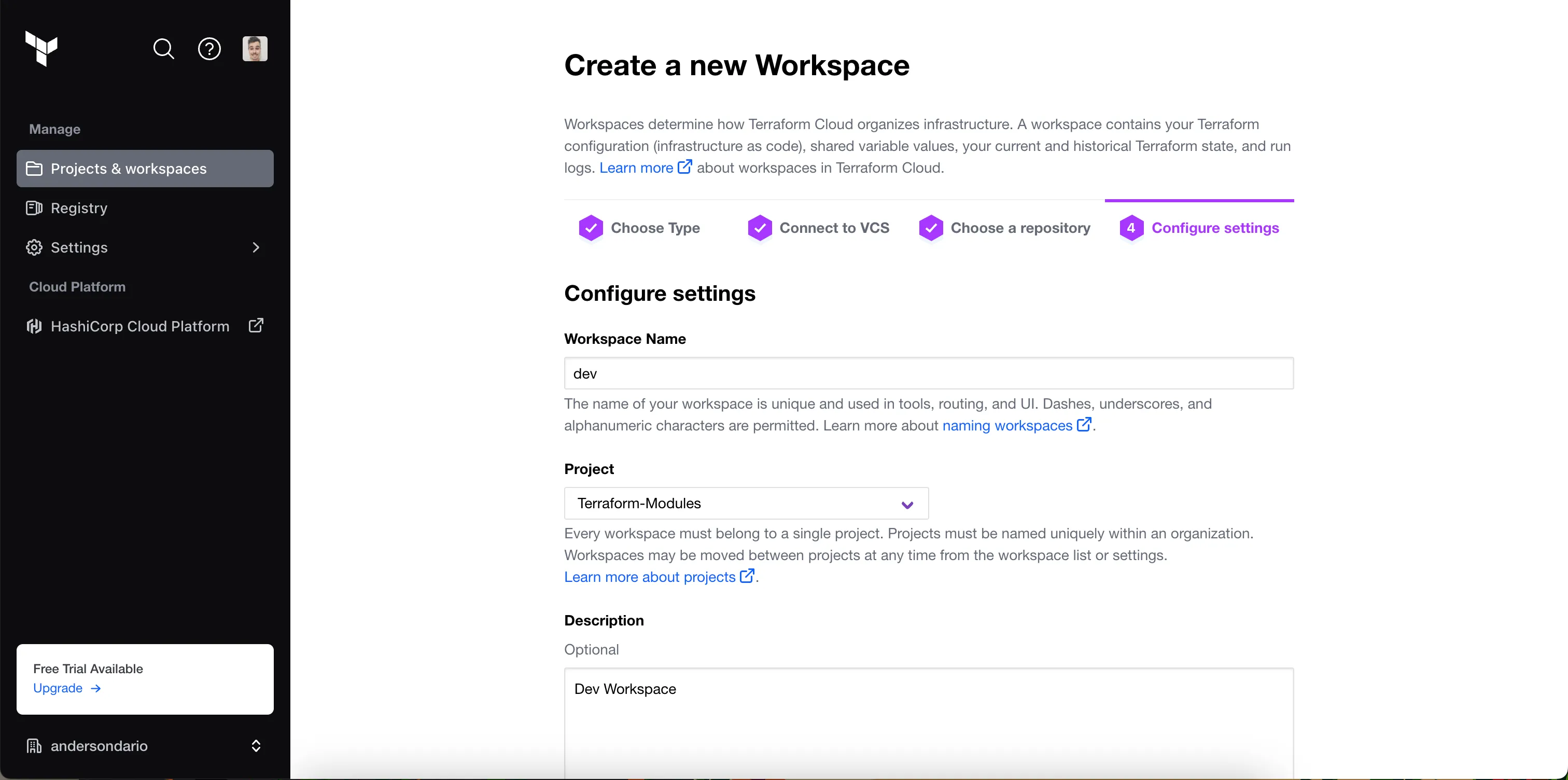
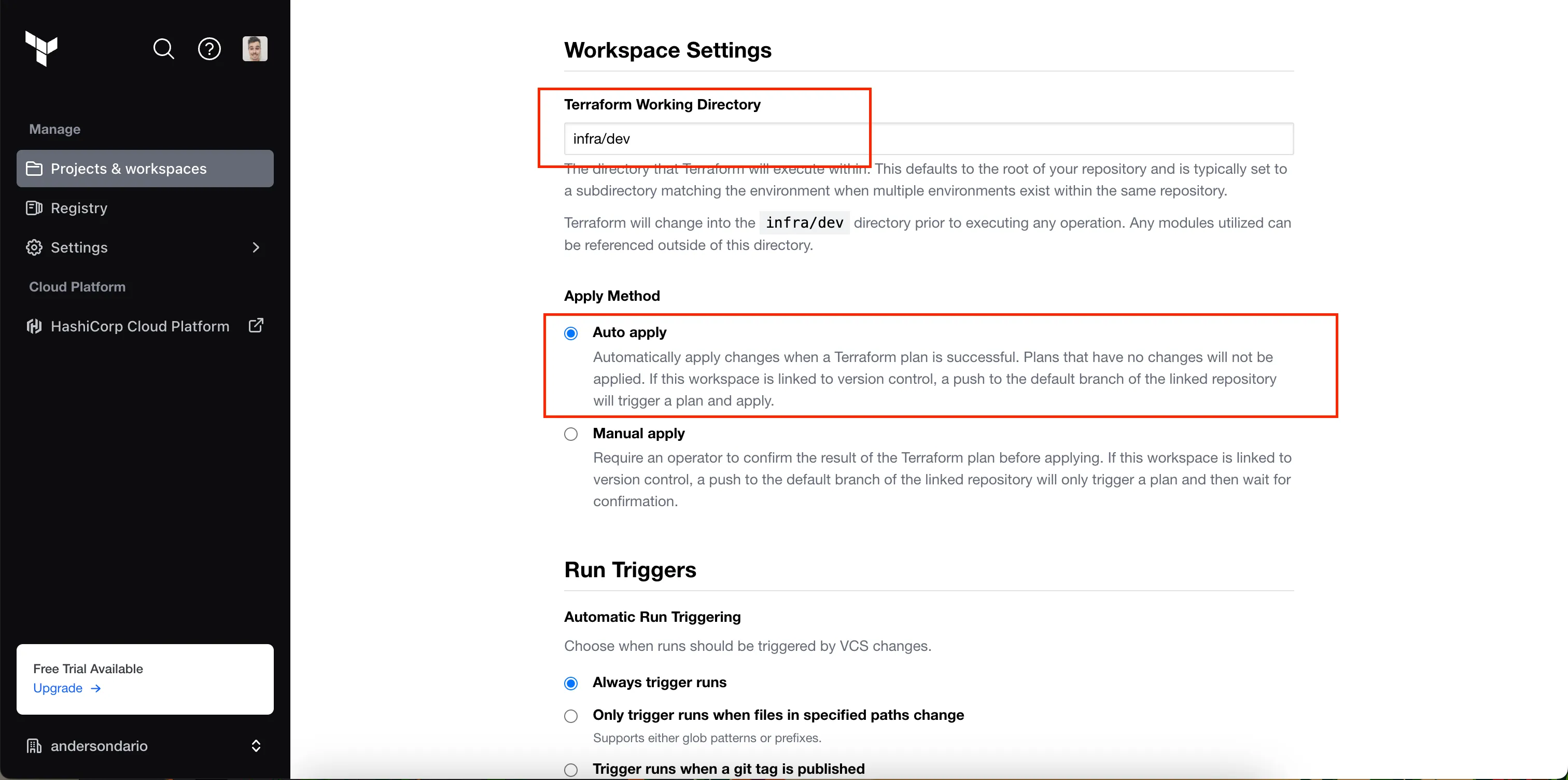
In the Advanced Configurations, I described where my dev code is located. In my repo, it is in the infra/dev subfolder, and for dev workspace, I also would like to Auto Apply changes.
Workspace Created.
- Lets add our wokspace variables. For that, click in the namespace, and then, in Configure Variables button.
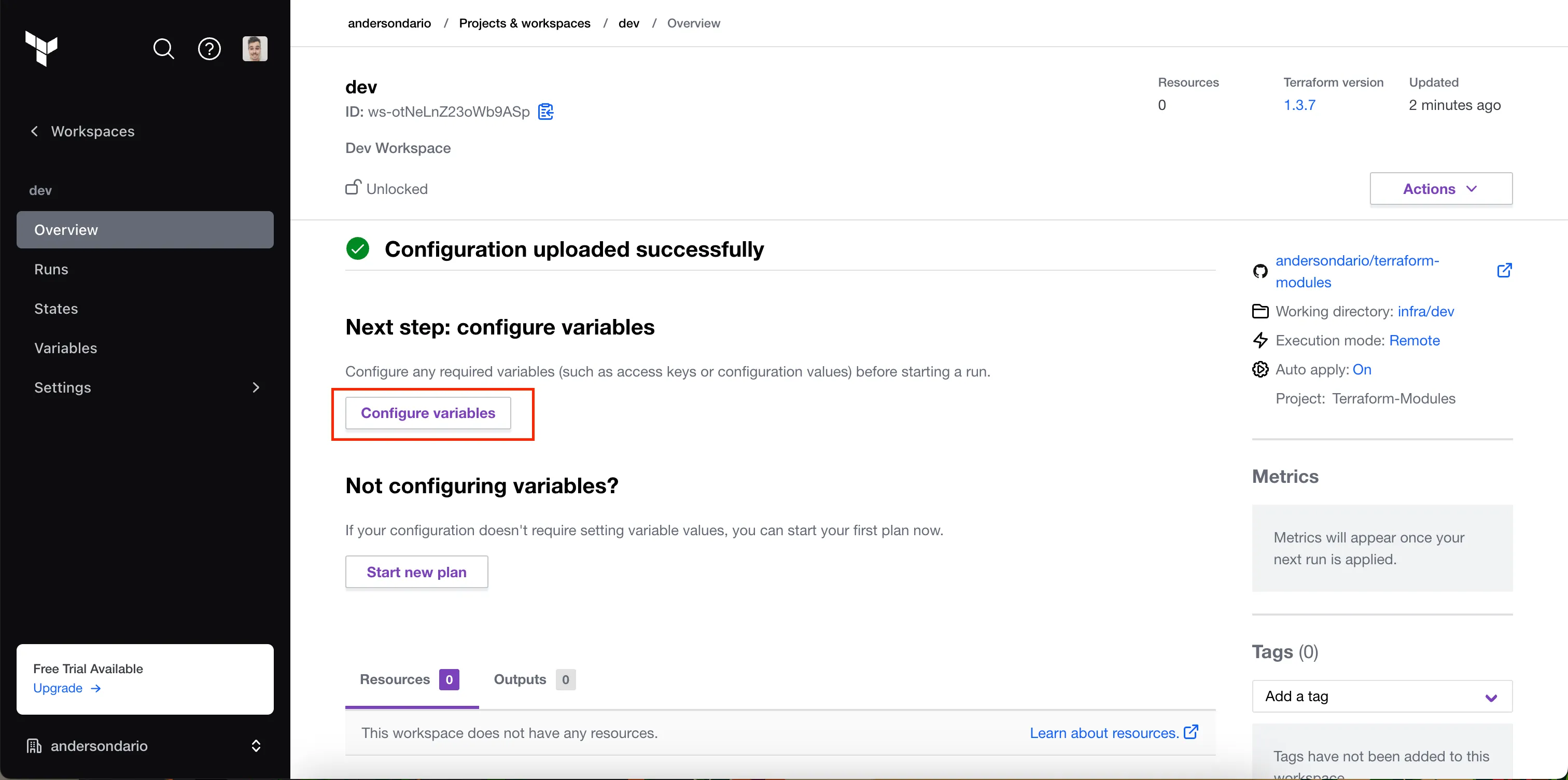
Configure variables
In my case, just two:
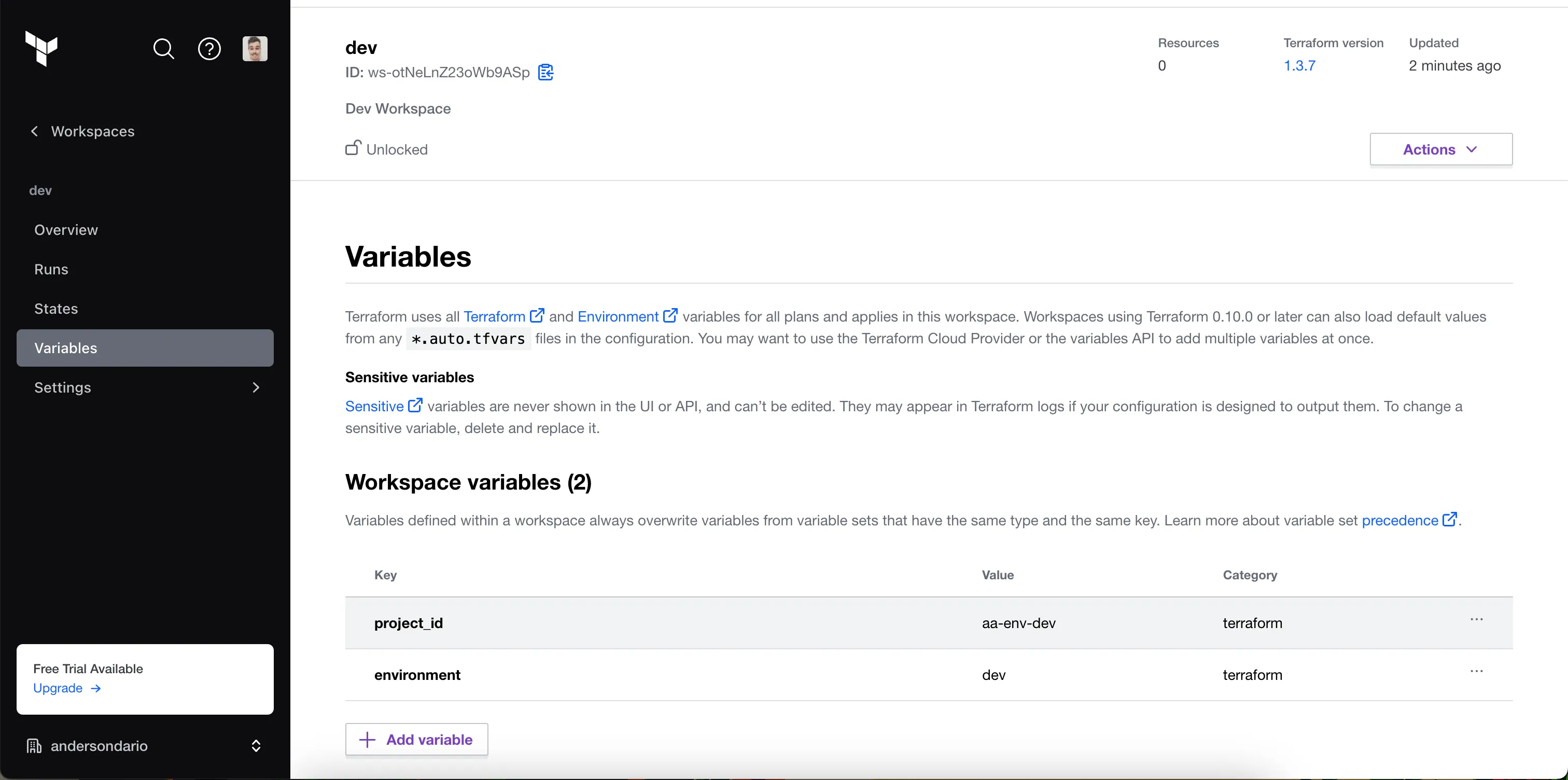
Variables
Now, we can see in our Pull Requests Terraform Cloud being executed:
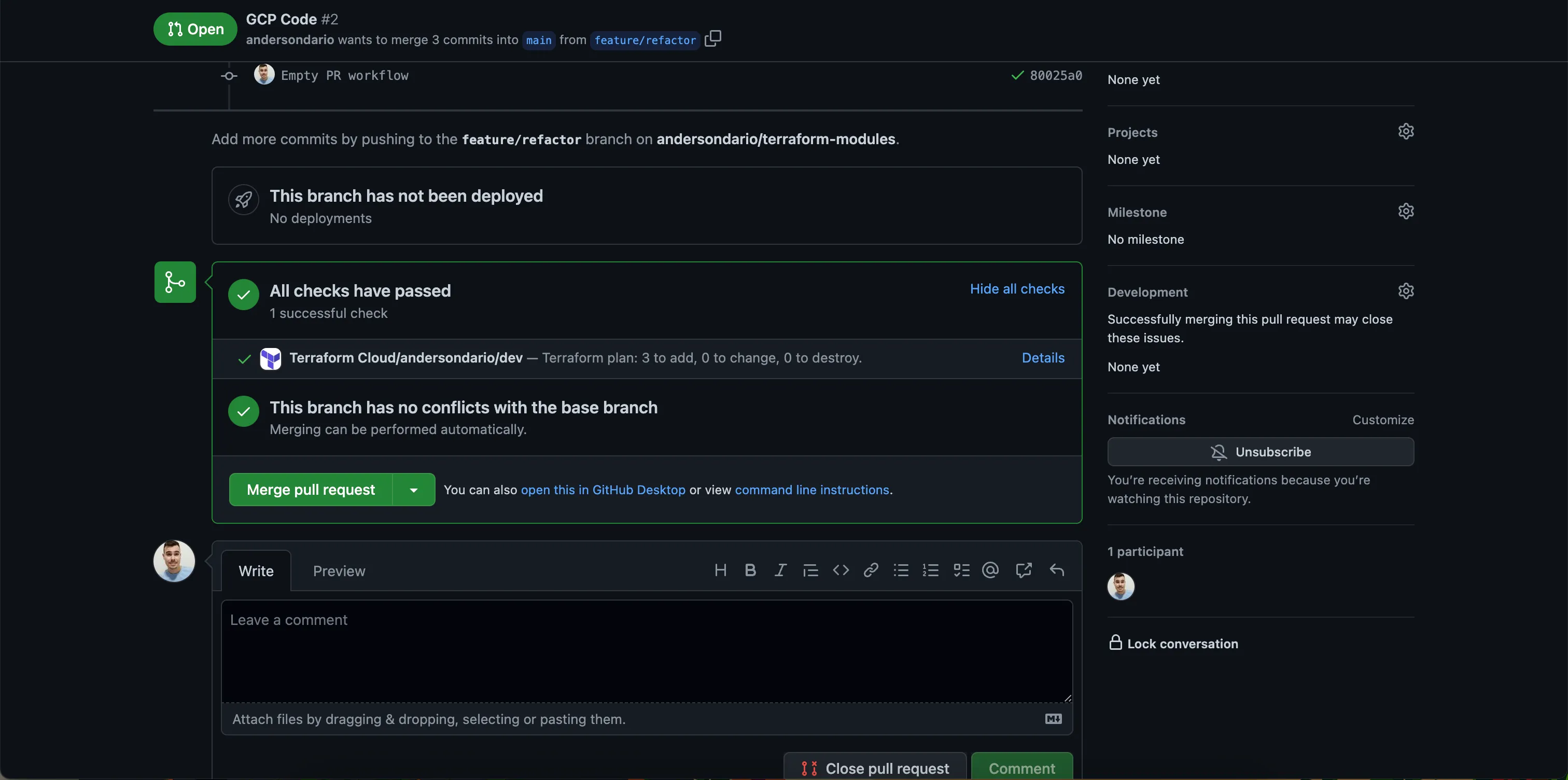
PR Check
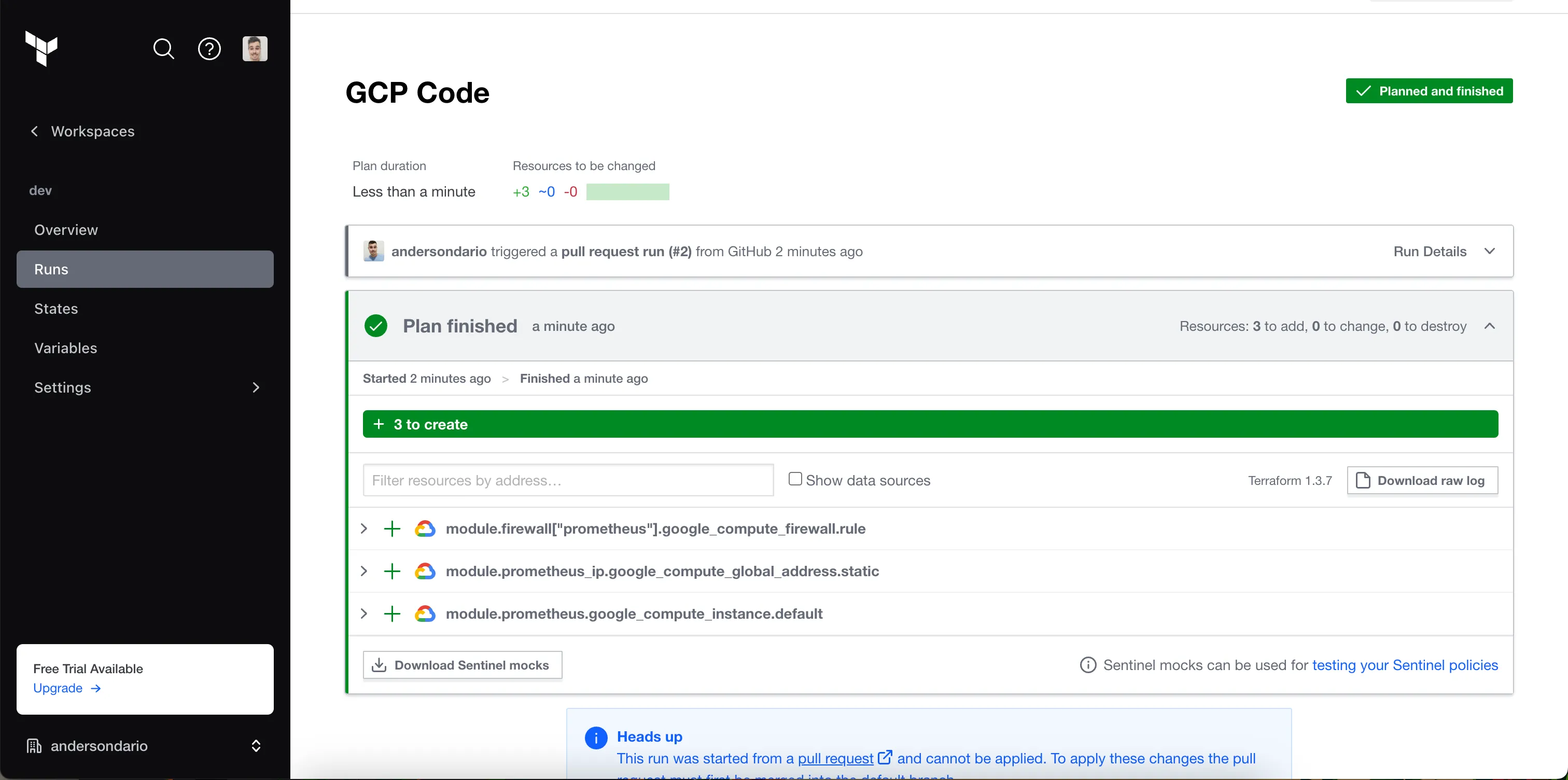
PR Plan
And, after the merge, another run, now, applying the code.
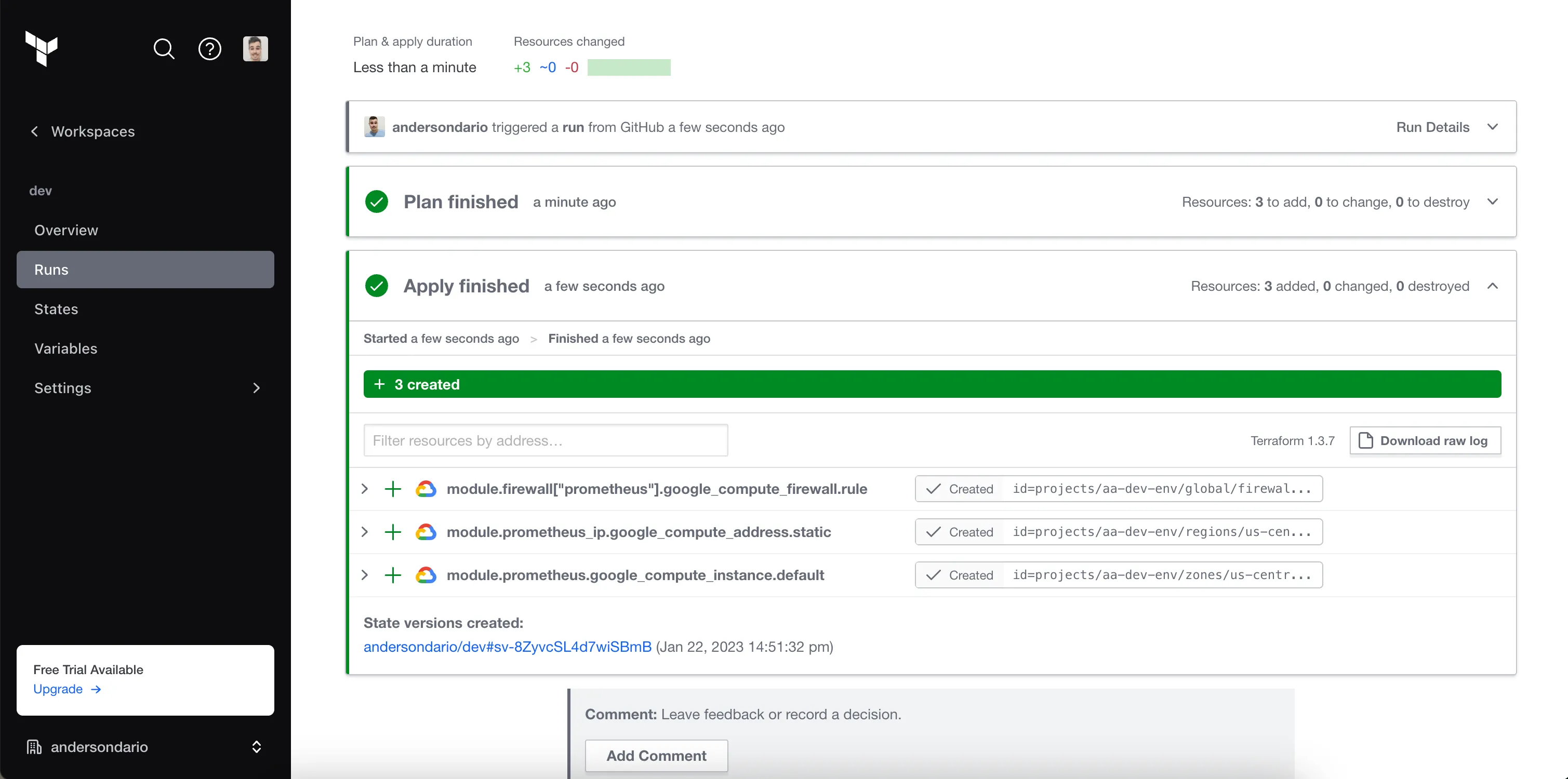
We can see our VM created in GCP:
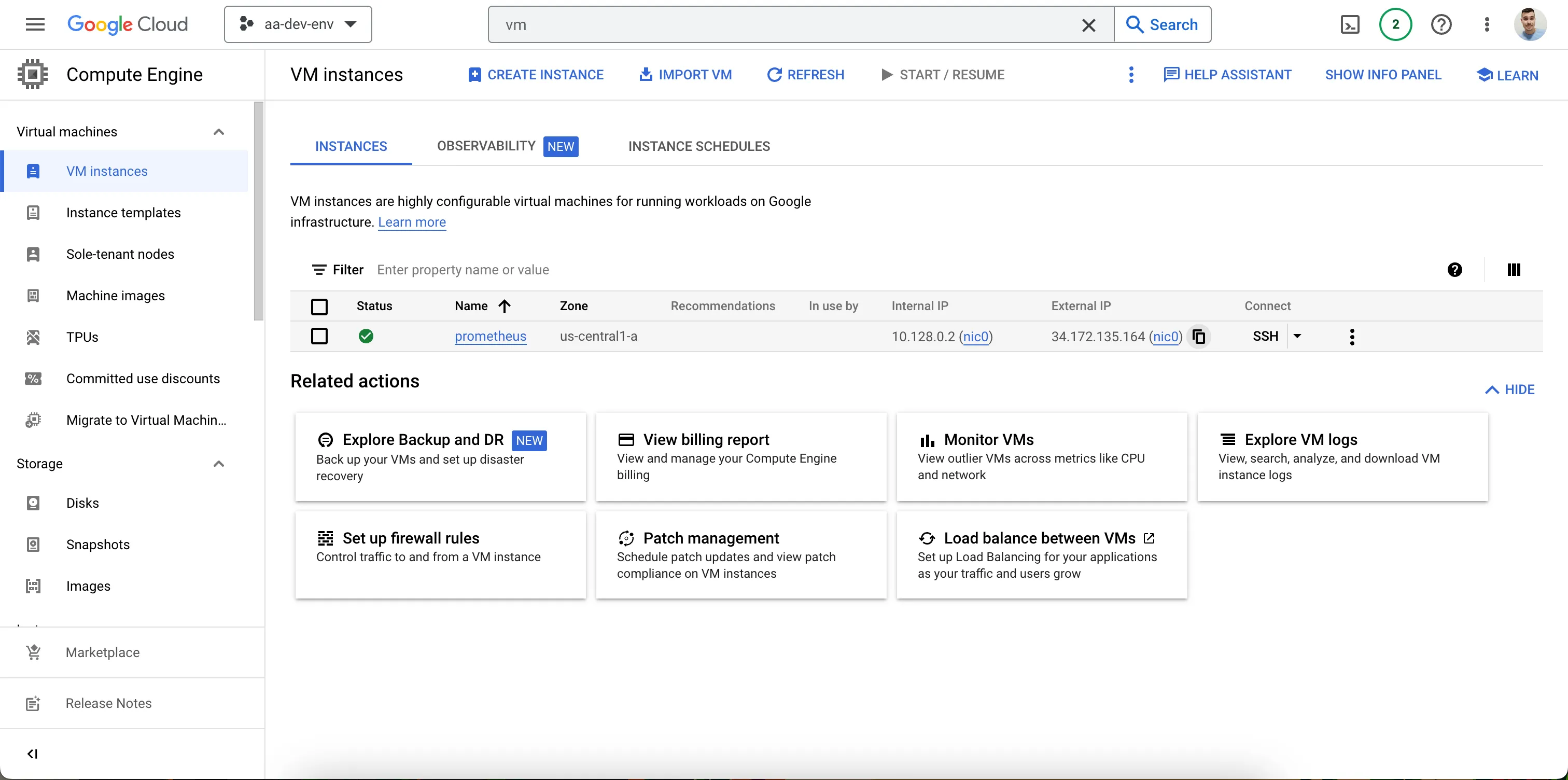
Prometheus VM
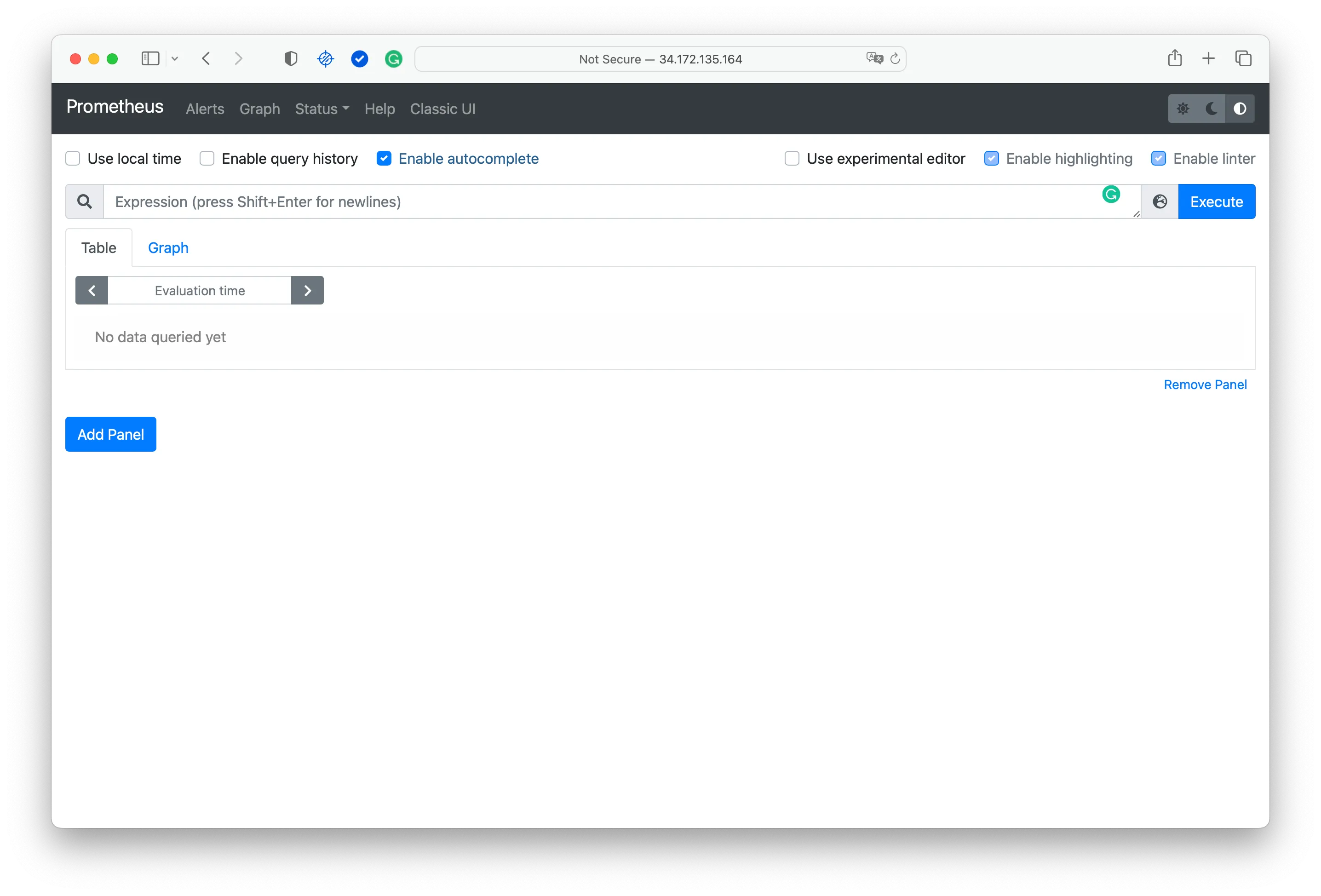
And then, we can access the public IP and check that our Prometheus Server is running correctly
Tips/Next Steps
- Create sub-folders for other environments.
- Create workspaces for other environments.
- If PROD please consider using Manual Apply.
- Refine which code files/directories will be watched to trigger the runs (Workflow configuration)
Useful Links and References
- Project Repository
- Google Cloud Provider — Configuring Authentication.
- Google Cloud Provider — Configuring Public IP
Support
If you find my posts helpful and would like to support me, please buy me a coffee: Anderson Dario is personal blog and tech blog
That’s all. Thanks.